
AWS re:Invent greetings from Wednesday
My Wednesday started with a small sunny walk to the MGM Grand Conference center for breakfast and sessions. It is remarkable how life changes just after a block from the Strip. Here is one picture where you can see hundreds of meters of wall of enormous 9 floor garage buildings.




Morning sessions
Architectural innovation for highly distributed edge workloads (HYB307)
The session was mostly about AWS Outpost instances located in on-prem. I missed the hybrid term when choosing the session. I was expecting to learn more about local zones etc. AWS Outpost is basically an extension for your VM related workloads to on-prem. For example data center cooling, networking and physical security are customer’s responsibilities in a shared responsibility model. AWS owns the device and provides 4h SLA service coverage for it. The Outpost connects to the AWS control plane via multiple VPN’s managed by AWS. It has local network connectivity. Basically it is good for some latency critical software or for regulatory purposes.
Reimagine the security boundary with Zero Trust (SEC324)
The first half we discussed the new AWS Verified Access (AVA) service. It provides an important solution to have “micro VPN” from the user’s browser up to the VPC’s private load balancer. The client is first authenticated via normal SSO (eg. AzureAD). Then the Chrome/Firefox browser plugin creates a secure connection to AVA endpoint. Finally the client can access private VPC ALB/NLB if the access is granted.
In AVA the access to applications can be controlled at a detailed level via access groups and their policies. Software defined perimeters (SDP) can be adjusted. The AVA service creates access logs in Open Cybersecurity Schema Framework (OCSF) format. Standardized log format makes integrations to SIEM service easy.
The pricing is something to notice. If we have an application which has three environments, the service will cost us 21 000 USD in three years plus 0.02 USD/GB for data transfer. Still I think the price is relatively high if your app is not truly a large scale enterprise app or you have multiple micro services = applications used by the client.
The other half we talked about basics. AWS has many fundamentally important services that people don’t associate with ZeroTrust services. AWS IAM eg. with AWS APIGW creates a solid managed solution to control service access. Inside a VPC, the usage of security group relationships (SG A can connect SG B’s port 443) makes a huge difference. PrivateLinks to share services between VPCs’ is again a solid structure. Also new AWS VPC Lattice a.k.a “consolidated service mesh” looks promising to great cross-account service mesh networking.
The lunch at Caesar Forum was great.


Afternoon and evening sessions
AWS network architectures for very large environments (NET303)
When you are using a single AWS account for multiple workloads you might end up with hard limits that 99% percent of AWS users don’t know exist. Before there was a 50 000 ip address limit under the hood (not public information). During that period AWS monitored each VPC’s IP usage. When the usage was over 10k AWS proactively contacted the customer to discuss needs and maybe to rethink the architecture a bit. Nowadays the limit is around 250 000.

It was time to move to Caesar Forum by the re:Invent shuttle service.

Network operations, management, and governance best practices (NET305)
The session highlighted four network operations categories: collect, monitor, troubleshoot and analyze. The price comparison can sometimes relieve strange things. For example VPC Reachability Analyzer costs 0,10€ per run and Transit Gateway Route Analyzer is free to use. If you would like to monitor your essential routes every 5 to 10 minutes even the smallest fee can cost a lot at the end.
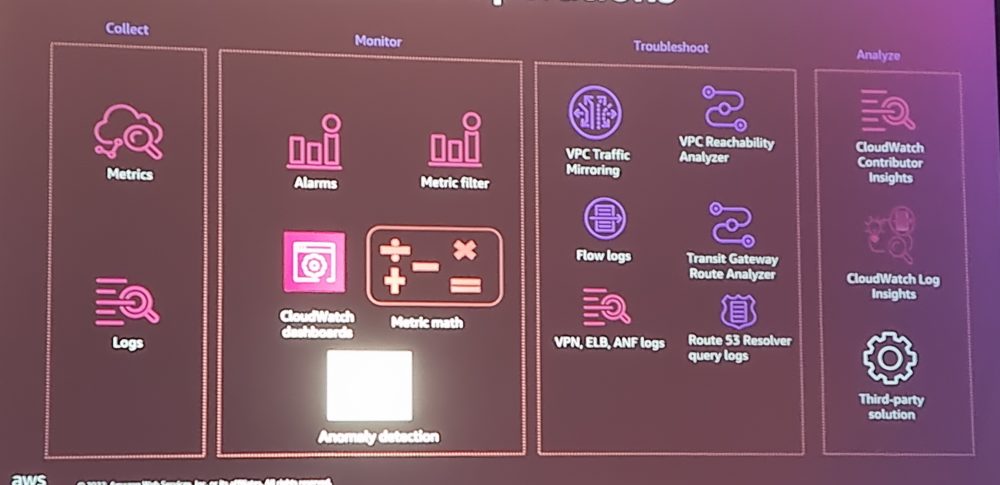
NetDevOps stands for network development operations. It is a huge cultural change for many organizations. I guess more than 90 percent of networks are still managed by ClickOps method, in a good scenario including documentations.
In Solita CloudBlox development we believe strongly to devops culture. For example if I need to add a new route to AWS TransitGateway or create a new Route53 DNS Zone, I will make changes to a branch in the GIT repository. After the PR of the branch is accepted and merged, it will automatically trigger the CICD pipeline. In the end of the pipeline AWS organization is fully up to date including the latest changes defined.
Designing a multi-account environment for disaster recovery (ARC319)
The session was about business continuity (BC). The basic explained solution was to have a reserved organizational unit (OU in AWS Organizations). In the BC OU you will have one or more BC accounts with very limited access. Each solution must follow 3-2-1 pattern: (3) 1 primary and 2 secondary copies of data, (2) 2 accounts and (1) 1 cross-region (or outpost solution).
In case when one or multiple accounts gets compromised, you need to be ready to restore accounts from ground up. In this kind of DR scenario you would need to retrieve secondary backup from BC account to newly re-created accounts. Old accounts would be locked and reserved for future investigations.

The cake vending machine
After a long day I decided to walk back to the hotel to write this blog post and to pack my luggages ready for Friday. Thursday is awesome re:Party again so I will be late at the hotel.
Every day I pass the cake vending machine twice in the Paris Hotel & Casino complex. Often there are a bunch of people using it. That’s all for today, bye!

